The antagonism between black hat and white hat strategies has been going on for years now. These strategies have been around since the existence of SEO. It seems they aren’t obsolete. On the contrary, they’ve persistently lingered around the SEO world and seem to be fruitful even in 2014.
We do not endorse or recommend the usage of these techniques. This blog post’s intent is to show how black hat SEO works in 2014. Some of the techniques presented below are not only black hat but also “crap hat” which is illegal.

Even if Google tries to update it’s algorithms as best as it can, to cover all grounds, and provide users with pertinent and valuable information in search results, black hat SEOs seem to always adapt and find ways of ranking high. The strategies that I will present below, aren’t exactly new, as you’ve seen them work in the past, in some version or another, but apparently they are still kicking and punching in 2014. We’ve seen these black hat techniques used by small or big businesses, but one thing is for sure: sooner or later you’re going to be spotted by Google. It’s your choice if you plan to rank fast and stay up in the SERPs only for a short period of time( hours or days), or build a strong link profile that resists the test of time.
Let’s look at how the famous “buy viagra” SERPs look like nowadays and what techniques were used to get a top ranking there.
1. Parasite Hosting
This approach refers to performing SEO techniques that revolve around generating pages on high authority domains that rank very good in Google. These pages point to a certain site they wish to promote, boosting their position, based on the host’s ranking. Basically they steal some of the attention the parasite site gets to enjoy its already earned authority in Google. As you can see in the picture below, the hacker placed the “canadian viagra” page on a Hotel’s site. The two topics, “hotels” and “viagra”, aren’t related whatsoever, so it’s clearly not a naturally generated page. Another fact about parasite hosting is that the owner of the host has no idea about this, and the page was created without his knowledge. Let’s see a quick case study on what techniques are working in the pharma area.
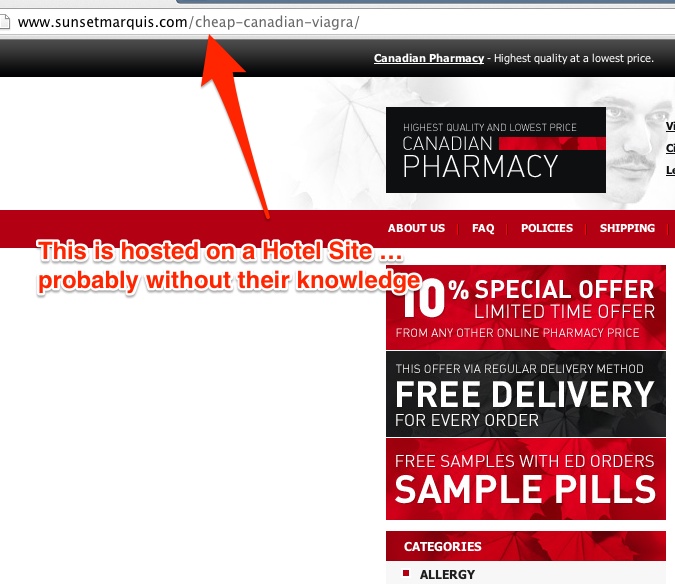
There are those that work hard and create a strong authority and there are those who parasite!
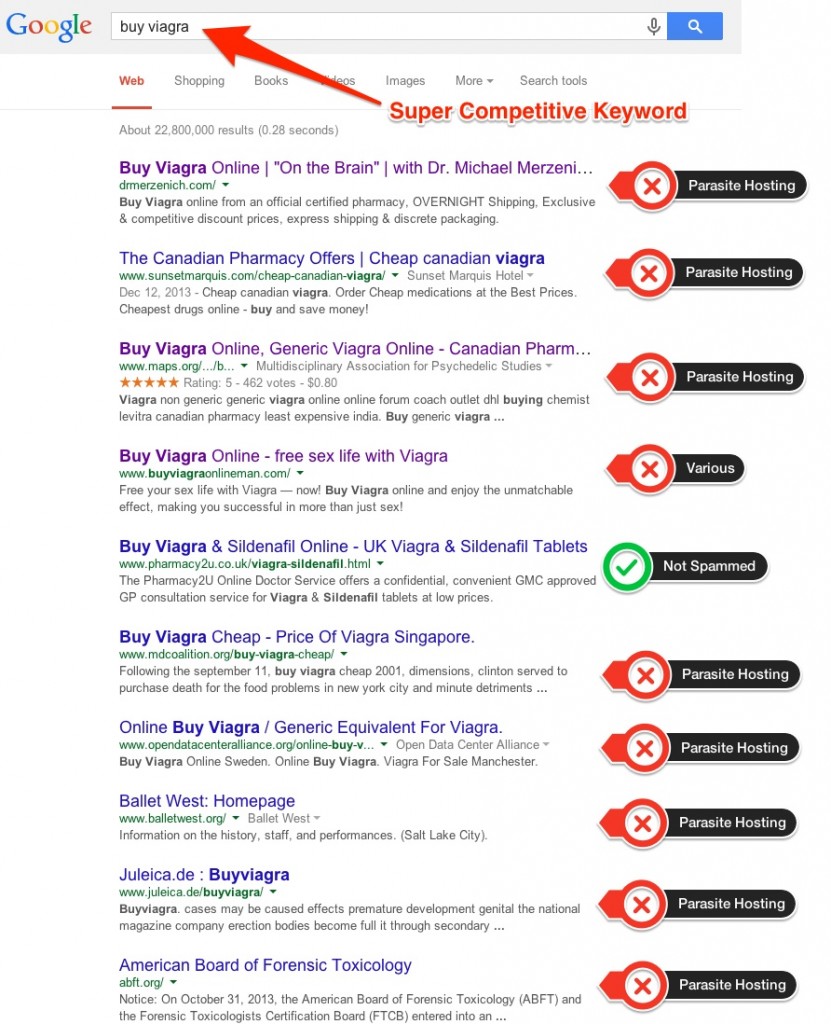
Going for super competitive keywords means a lot of effort and a lot of resources invested. In the picture displayed below you can see the blatant competition that’s going on over pharmaceutical keywords – from 10 results displayed on “buy viagra”, 8 of them are ranking using parasite hosting. It’s interesting how, after all these years and all the algorithm updates, these type of parasite pages can still rank pretty high in search results.
It proves to be a very productive strategy for Black Hat SEOs in 2014.
Some people would call this technique as being part of a category named “crap hat seo”, due to its illegal nature. This is because these people hacked the sites and hosted their own content there.
2. Google Bombing
It needs to be stated from the beginning that it’s not as life threatening as it seems, and you won’t see any explosions on your screen. We’re going to move from one strategy that has been around for some years now, to another one. The first time this term was mentioned was in 2001, by Adam Mathes. But since it’s first appearances, it slightly went from being a form of prank to a form of boosting pages onto the first positions of Google. It seems black hat SEOs can still exploit this technique by using consistent anchor text when linking.
We have a clear example of Google Bombing so you may understand how this black hat strategy works and how it affects a site’s ranking. If you’ll take a look at the screenshot below, you’ll notice that there is no historic data for this URL, meaning it’s a brand new page. The big link velocity spikes from the last days and there is an abnormal amount of links created just after a couple of days this page was created.
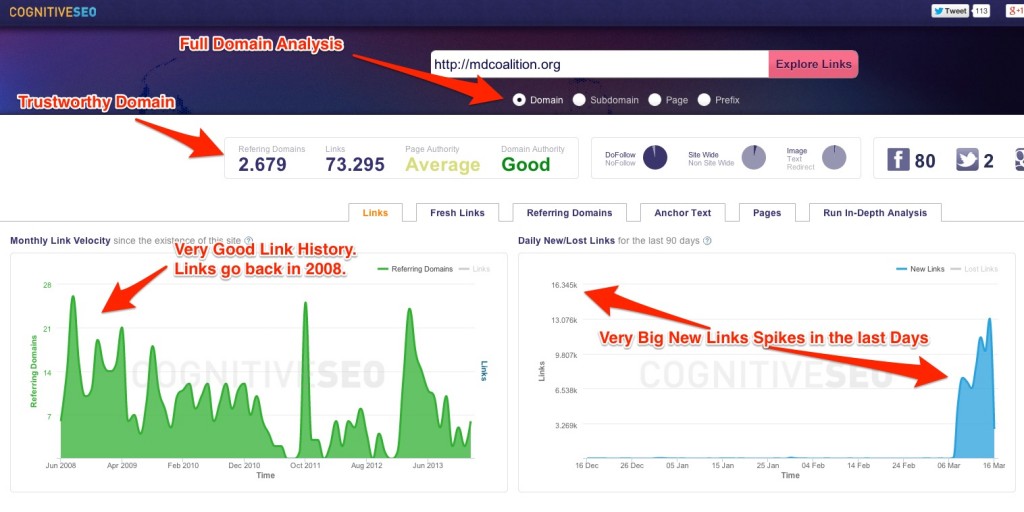
On the other hand, if we look at the whole domain on which the page was created, we can clearly see it’s not created with black hat SEO intent. The link velocity graphic for the whole domain shows a consistent link history that goes back to 2008, meaning that the site was steadily building links creating a solid authority. You can also see that for the last days, there are new link spikes that are very big and look suspicious. This black hat strategy may ruin a trustworthy domain.
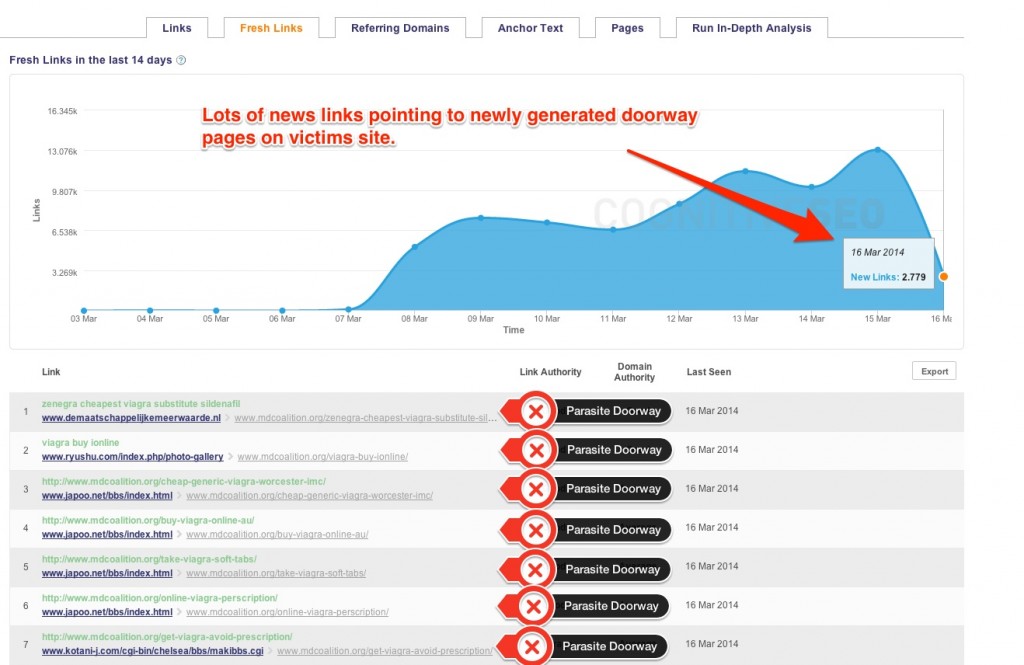
Without that newly generated page, the domain is performing very well and looks very natural. If you’re wondering just how many links are created to sustain the pages on a victim’s site, you can look at the image below. A lot of parasite doorway pages are created in order to redirect visitors to the final landing page.
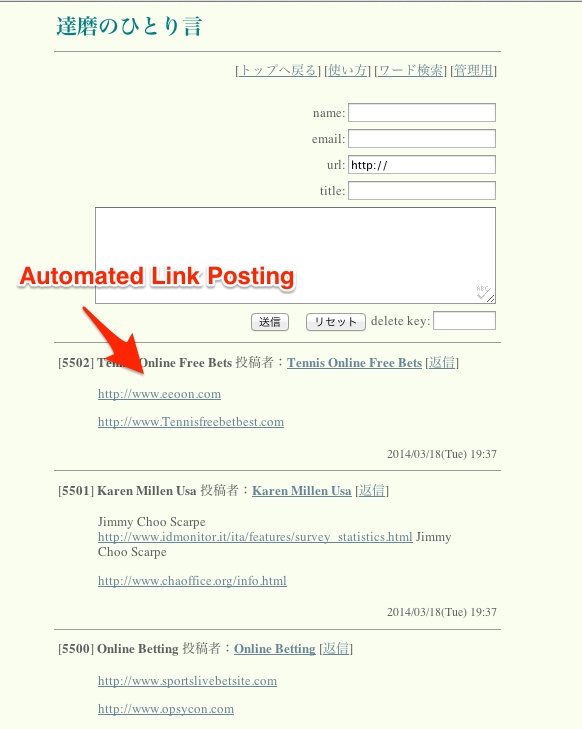
A lot of black hat SEO’s use automated software to generate lots of links on numerous sites, blogs, forums and web directories. Pretty much any place that accepts a text to be inputed on the page. These type of tools make spamming more effective, but only for a short period of time. These type of strategies won’t work on the long-term, since Google poured a lot of effort into creating an algorithm that identifies and dissolves such link schemes efficiently.
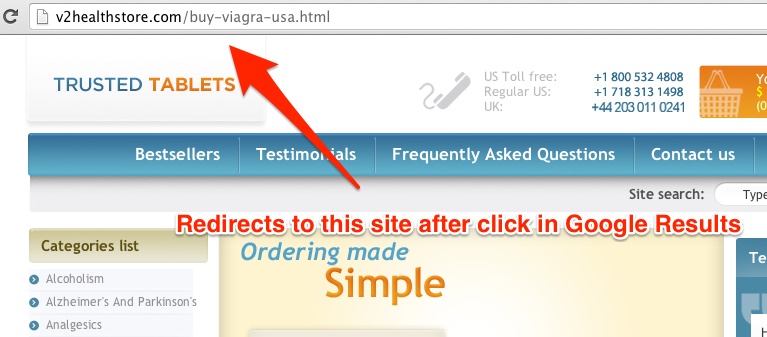
3. Cloaking & Redirects
By crawling your site, the GoogleBot scans your site and validates the data to be indexed and displayed in the search results. A website is considered to be using cloaking when it displays one page to the search engine spiders and another page to the users that click on the link from the SERPs. You can sometimes find yourself clicking on links only to find out that they have little to do with the description displayed in search results. Usually, those that are using cloaking and redirect strategies create multiple pages, all optimized for a certain topic using specific keywords.
Matt Cutts, the head of the Webspam department at Google explained cloaking in this video released a while back. This is important as it depicts how Google sees cloaking and how they classify it. It clearly states that:
There are no forms of white hat cloaking strategies that you can use for your site.
It’s made with the purpose of deceiving users or to present users and search engines with different types of content. When you’ll click on the link displayed it will take you to a page created to send traffic to the viagra selling site, or it will simply redirect to the site.
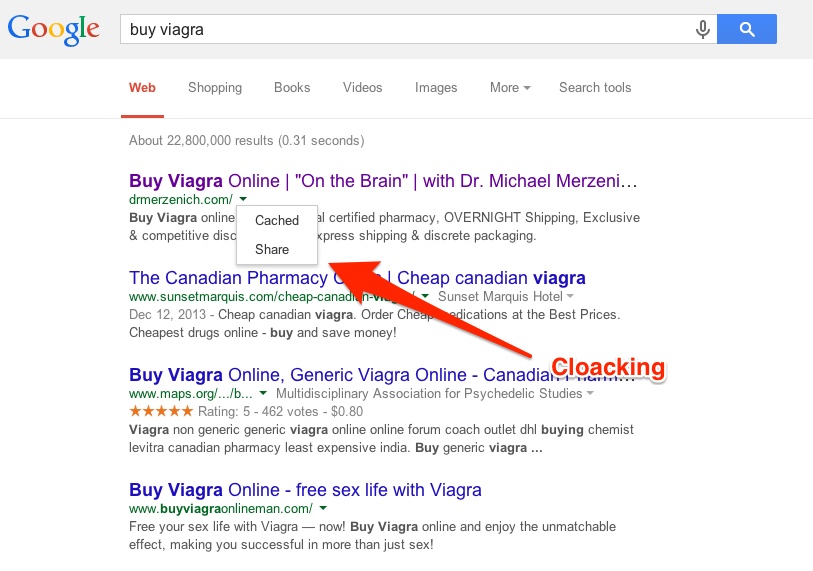
A lot of websites that have used cloaking and redirecting in the past couldn’t hold on to their site’s ranking for a long time. This tactic is still used in the present and you can clearly see an example in the picture below. If you’ll be curious enough to see how Google see’s the page, you can just click on the tiny triangle next to the link in the search results and then click on “Cached. That way, you’re going to be able to see the crawled page through GoogleBot’s “eyes”. To further understand how these techniques of link manipulation are still viable in 2014, you’ll have to learn how they work. In a nutshell, cloaking the site will have a script that scans search engine robots on one hand and human visitors on the other hand and classifies them after their IP address. If it’s decided that the visitor is human it will be displayed the content you wish to display. But if it’s GoogleBot, it will be set to be directed to an optimized page in order to pass as high ranked and valuable. Below you have a screenshot on the site it redirects after you click on the link in the search results.
Conclusion
Parasite hosting, and his close cousins Google Bombing, Cloaking and Redirects are among the select types of black hat strategies that are still being deployed successfully in 2014. Since they don’t serve any purpose other than manipulating a site’s ranking and they offer no real value to the user, they have a rather short life span. I need to mention the fact that, left isolated, any of these black hat techniques could not make a site rank too high. The real power is harnessed when they are used together.
I want this post to act as a notice for the ever-growing SEO landscape, that Google is still an algorithm that is still exploited by the Black Hat SEOs. Even if Google greatly improved its algorithms in order to better to detect unnatural links and find shady patterns, I do believe that there is still work to be done when it comes to super competitive keywords such as the one presented here.
Photo credits: 1
 Site Explorer
Site Explorer Keyword tool
Keyword tool Google Algorithm Changes
Google Algorithm Changes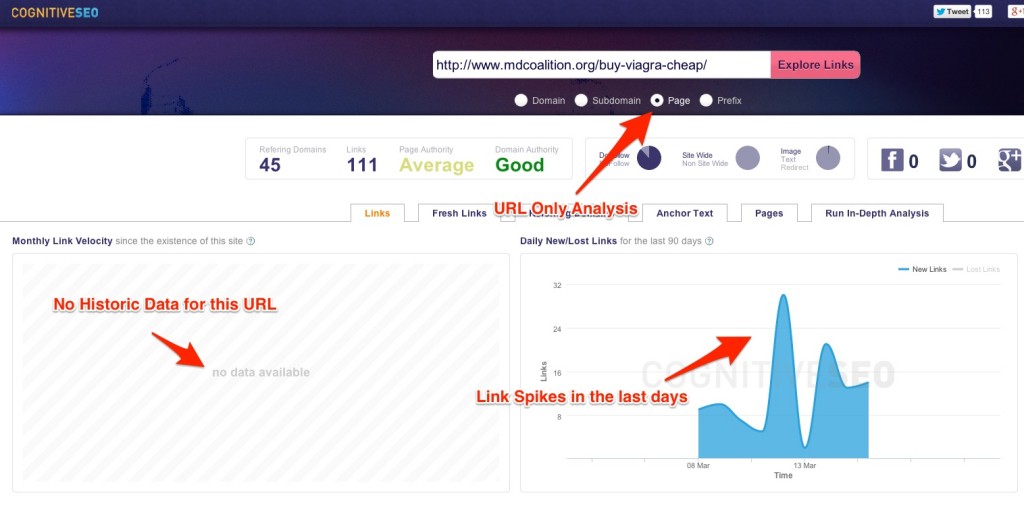


the second case doesn’t require the rest of the domain to be healthy anyway. unfortunately i see the spammers still getting their way to the first page for competitive keywords with new domains spammed like there’s no tomorrow (but they have a tomorrow, and a day after tomorrow too, since Google seems not to care too much about certain industries…)
that is a different technique 🙂 the Google Bombing is not just blog comments and forums automated. It is a full range of sites they can hack and introduce the links. shown in a study here https://cognitiveseo.com/blog/1914/new-black-hat-technique-beats-the-google-penguin-and-emd-updates/
I think we can also consider cloaking website that hide text to users but this is visible in the source code.
Usually it’s hidden by
clocking is a technique that hides text to the search engines only. Hiding the text to the user is another technique.
Parasite hosting seems to be working very well. I mean, looking at the SERP result for that specific query, the page was dominated by parasite hosting stuff!
But my question is- won’t such techniques be noted and acted upon by Google? Won’t using these strategies be harmful in the long run?
Arun
they already are harmful. they only work for days. but these sites are dumped after that and the process is replicated on another one. It will stop working in the future for sure. But now it works.
I’ve also noticed that many industries are STILL dominated by low quality directories, blog comments and spun content. It’s strange to see after all of the updates over the last couple of years, but I suppose Google will never be perfect and will always be fighting with two sides of a coin.
Great stuff.
indeed. but less than it was. I think it is only a matter of time until Google cleares them “all”. (almost “all”). So you should start to think about those times if your site has shady links and take action on the strategies you need to apply now.
Hopefully Google does something soon to sort out the parasite hosting issue, it’s really annoying seeing those links at the top of SERP’s.
There are also particular event based niche websites that easily rank in Google for main event keywords. People are cashing thousand of Dollars in a single day using these techniques.
Hoping that Google will rank authority sites higher in SERP than these crap copycat websites.
Have heard of Parasite hosting and Google bombing for the first time and hope that this parasite hosting issue is resolved soon by Google.
Hi, in the case of sites that have a lot of graphics and little text, like photographers websites, by what method can add text and H1/6 tag seen by spiders but not from the browser without being penalized in the future? How can remedy ?
google bombing aka blasting backlinks to a certain URL dominated the most, also it is still working as of now.
I’m a SEO Consultant for big e-commerce sites, my clients got BOMBED thousands of spam links/day and we waste lot of time disavowing. I dont know when i can tell them to stop disavow spam link without facing any penalty risk.
sorry to hear. that is why we created the unnatural link detection tool and automatic email notifications on it in order to make your life easier in this kind of situations. this technique still works it seems.
Yes, but who will trust a page with parasite hosting? l think people are getting more and more concerned today about eshops and websites.
the usual user does not know this. it is invisible to him.
I was using link building strategy some time back but my website started getting push down from google .. In the beginning i was not able to find the reason but after a bit of research i found out that google has restricted link building to quality backlinks only and if you start link building just like that , get ready to get panalyzed
i am doing work on pharmacy. i see our competitors they are very fast for me and they do advance work like black hat seo strategies but no problem one day i will beat them and always analyses his all activities and record it and i say daily many competitors beat me but my question is how is possible or say to google failure who to google rank the my competitors without backlink and without any website structure data good health and also bad DA PA according to me so what i do to beat them please guide me sir Some Keywords please check and more other keywords i am waiting for your reply