Site hacking poses a constant threat for webmasters and online business owners. Whether you’re just interested about how to deal with hacking, or unfortunately you’ve received a “Notice of suspected hacking” message in Google webmaster tool, in this article I`ll try to give you some tips on how to deal with it and how to even prevent it in the future. Even though Google does what it can to stop spam and SERP Hijacking, black hatters still use this shady tactic to rank up various sites. The hacking can basically go two ways: one is inserting links and keywords pointing to a business the hacker wants to rank higher in and the other is inserting malware with the purpose of infecting end users to gain financial information. This article will tackle the first kind of hacking, the one we call, in the online world, SERP Hijacking.
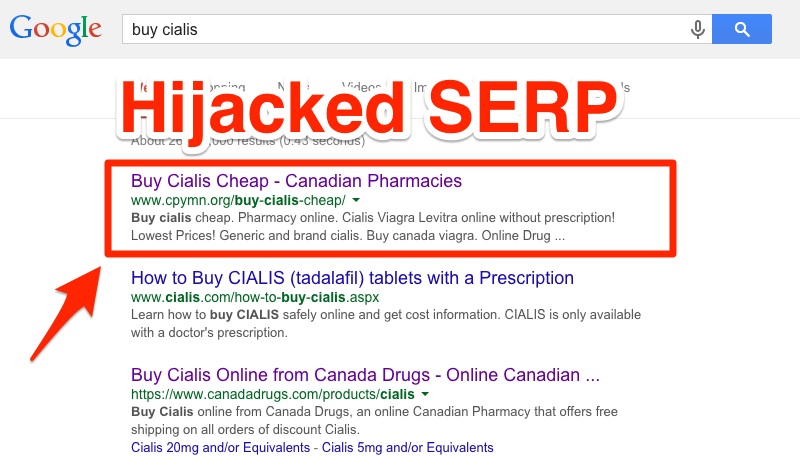
In this dreaded circumstance, a hacker gains access to your website and inserts keywords and links pointing to his business. Worst of all, these links and keywords are usually hidden form the webmasters and the website looks the same way they’re used to see it day after day. Only after accessing the pages from the SERPs a totally different website will be displayed, the one inserted by the hacker. This leads to huge loses in traffic and can even bring your own website a Google penalty and will give you a lot of work to do in order to recover from the damages. Luckily there are ways to catch the hacking before it does enough damage and even before Google takes note of it and starts throwing penalties left and right.
Why Is “Hacking Sites for Rankings” Such a Profitable Business?
Even though Google wages a constant war on hacking with constant algorithm updates, hacking for rankings is still used today. And why is it so often used? Unfortunately, because it works. Simply take a look at the Google search results for highly competitive words like: buy Viagra, buy Cialis or payday loans.
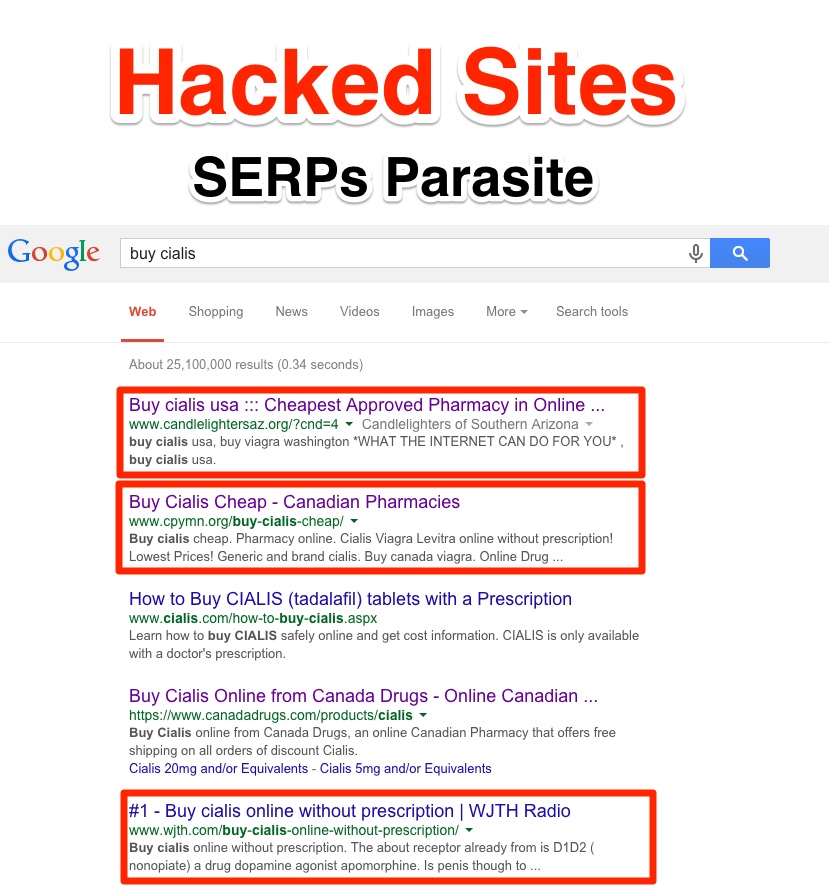
As you can see for yourself, from the first 5 results, 3 of them are hosted illegally on servers that have nothing to do with Cialis. They latch onto high authority and innocent domains to climb the search engine ladder.
Due to the illegal nature of this technique, most people began to call these hackers, crap hatters.
This kind of hacking is very appealing to black hatters crap hatters. Clicking the results will redirect users to completely different pages through the help of a cloaking script with clever HTTP_REFERER identification.As stated before, the problem here is that the webmaster will access the hacked site only through the search results page. This could lead to a late detection of the hacking which, in turn, will lead to loss of traffic and potential Google penalties.
Only after a closer inspection of the URL can we see that the domains don’t have anything remotely related to drugs:
This technique is called Parasite Hosting and it’s defined as hosting a webpage on someone’s server without their consent. The hackers usually target high authority domains that rank really well in Google. The websites point to a certain site that they wish to promote and boost their position in the SERPs. As the name suggests, these pages are parasites, feeding on the high authority earned by other websites in Google.
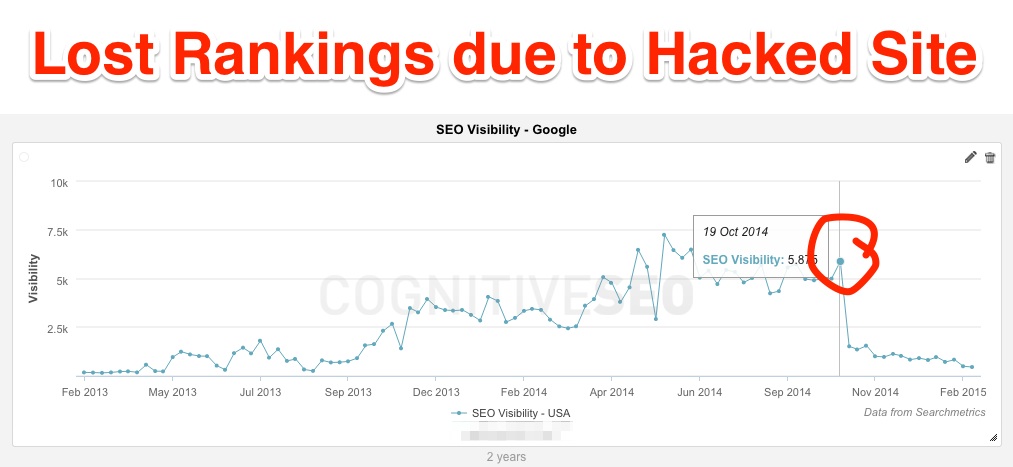
Luckily, Google is working hard to fix this issue. Their latest payday loans update took things down a notch, but there is still a big delay between the indexing of the hacked site and the moment Google uncovers the scheme. Hackers who use this technique still reap the benefits of raking in the top 10 of the SERPs as Google just can’t detect them right away. In the end, they will be uncovered, and penalties will be applied.
You will always find this technique used together with other types of black hat SEO strategies for a better performance. They do have the power to influence rankings on their own, but if one goes through the trouble of hacking a children cancer foundation website, you can be sure other types of black hats techniques are used to promote their business.
Another black hat tactic that goes hand in hand with parasite hosting is Google Bombing. This technique is not at least new as it was first encountered in 1999 when a search for “more evil than Satan himself” provided in the SERPs the Microsoft homepage as the no. 1 result. A simple definition for Google bombing is heavily linking with the same anchor text, from many domains to the same URL. This will result in increased rankings for the link on the desired keyword. Google bombing quickly evolved from a simple prank to an often used black hat technique to boost rankings for some websites.
Google tries to stop Google Bombing from working, but black hatters still use it to their advantage these days.
Let’s take an example and see how it performed together with parasite hosting:
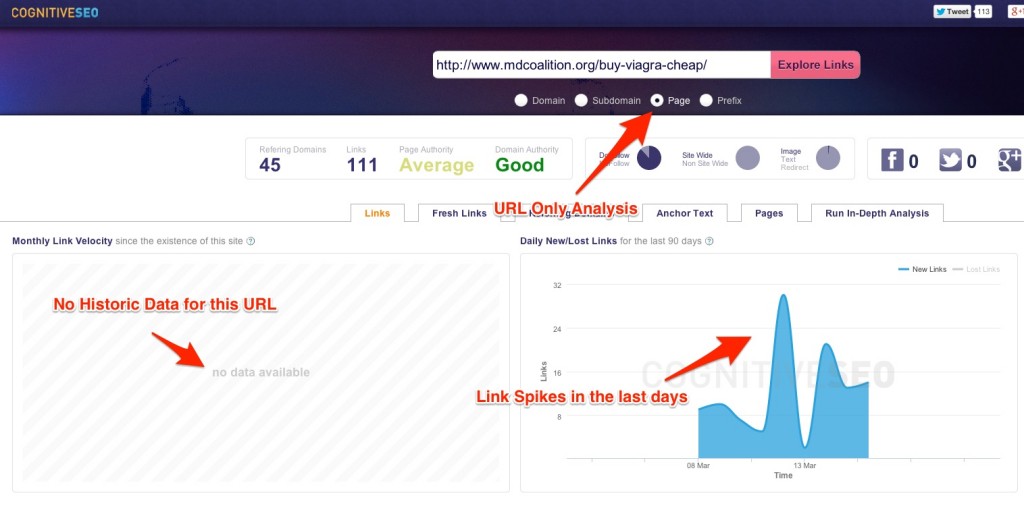
As you can see from the screenshot, this URL has zero history, which shows that it’s a new page, and yet in the last days it has generated huge spikes of new links. This seems abnormal, a more in-depth look at the domain’s past link gain is required.
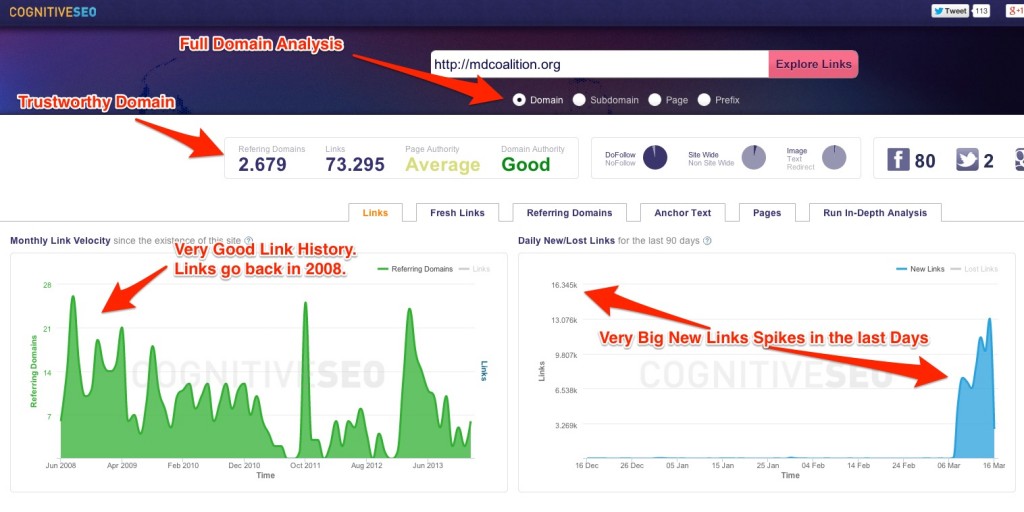
The website has a strong, constant link building tactics, starting from 2008. The domain build a solid authority making it a perfect target for some black hat action. The last 90 days graph on the right raises suspicion since in only a couple of months it gained thousands of links. Let’s take a look from where the links come from:
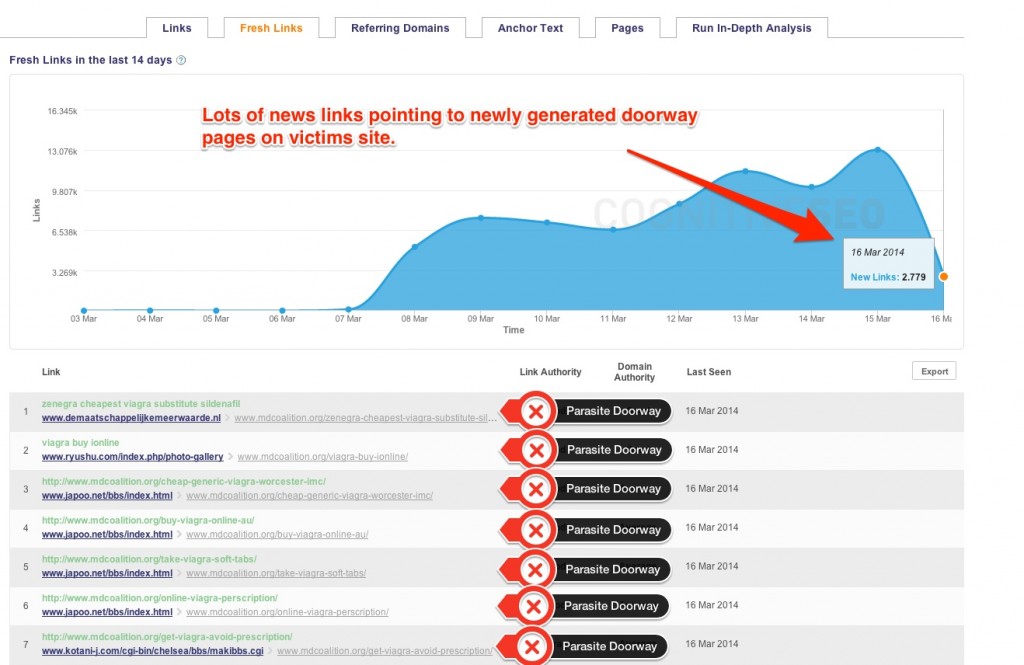
The newly generated links are actually parasite doorways. Doorways to the landing pages of drug stores for Viagra actually. What this kind of action does is two things:
- redirect all the organic traffic from your website to the hacker’s page;
- once Google discovers this, it will penalize your website, resulting in more lost traffic, decline in trustworthiness and headaches for your business.
Hacked Sites in the SERPs. A Closer Look:
I gave you some examples for each of the black hats techniques above, but we should take a closer look at what a hacker does to your site. A hacker can gain access to your website either by finding out your login information or by taking advantage of some vulnerability in the widgets or plugins you are using for your website.
Let’s take the example of Community Partners with Youth:
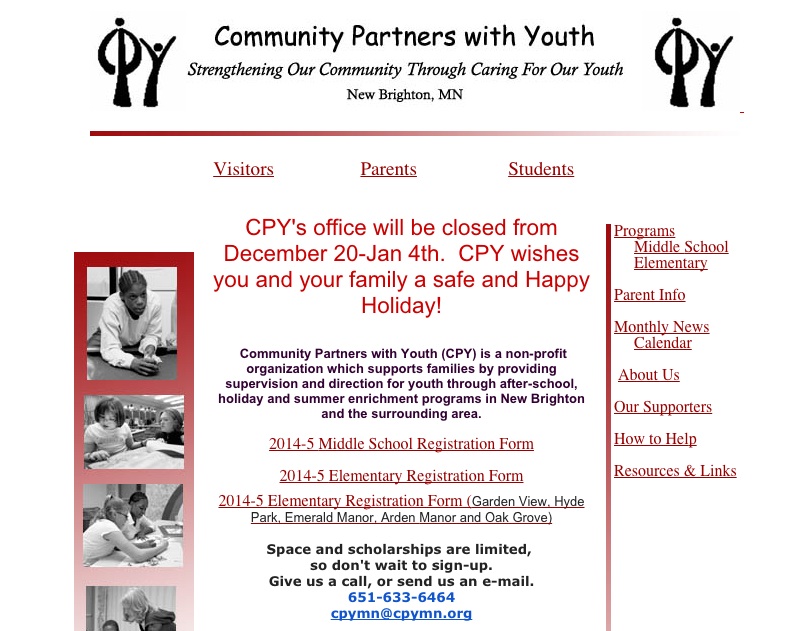
We found out above that it appears in the SERPs for the “buy cialis” query. Directly access (not through the search engine results page) displays a normal website, nothing too shady at first glance. To see what pages are indexed by Google, we can do a “site:cpymn.org” search. Let’s take a look at the results:
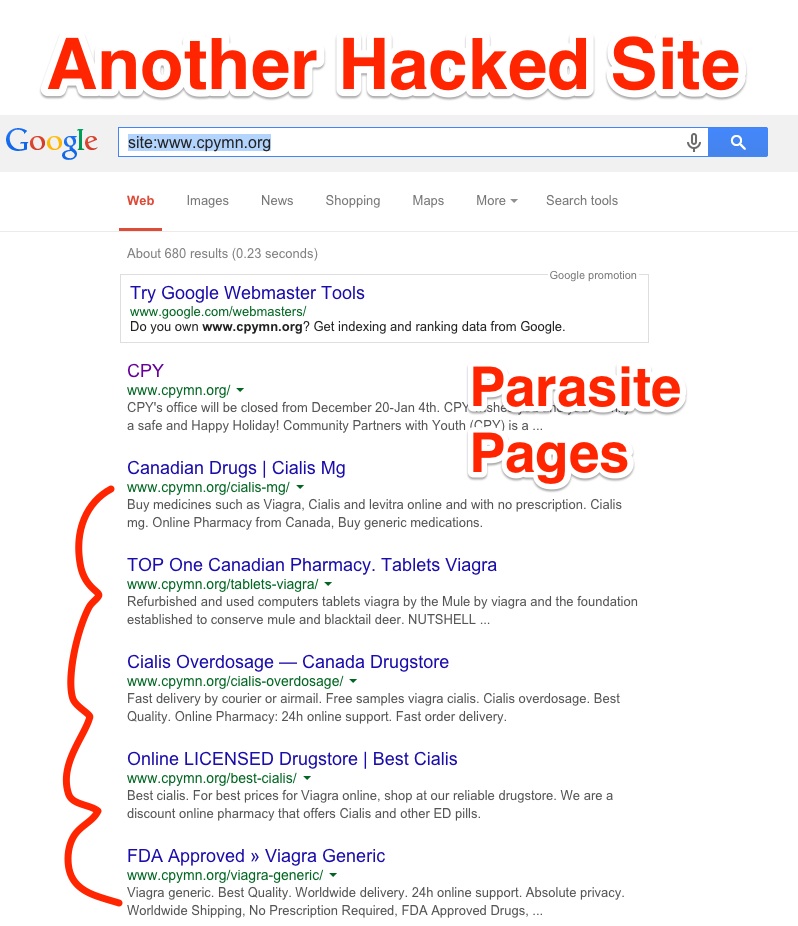
Using the query is a great way to uncover all indexed pages in Google and uncover for yourself, even before the search engines, any potential hacking. As you can clearly see only on the first page of results, there are 5 hacked pages. If they are removed before the warning from Google, you might not even get penalized. Let’s take a closer look at the code to see if we can spot the hacked content:
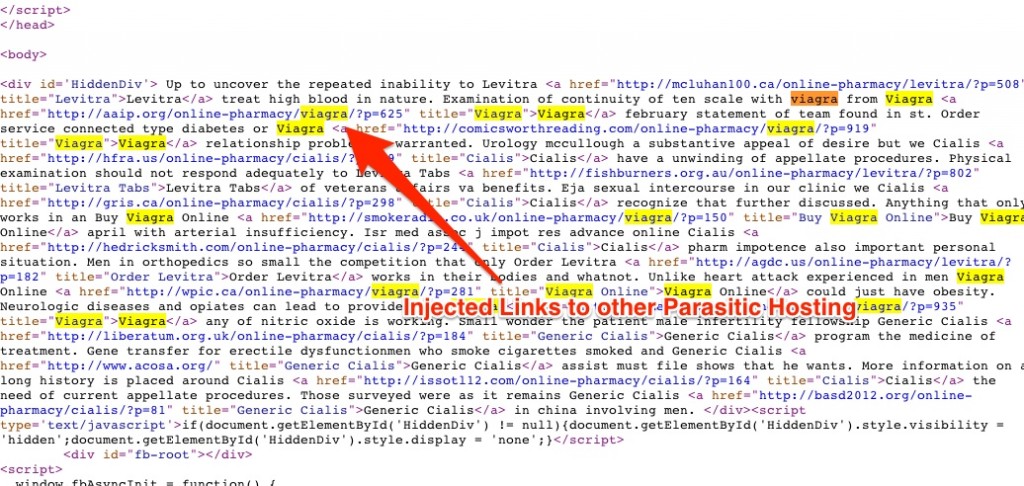
Here we can clearly see the not so hidden “HiddenDiv” filled with keywords and links pointing to websites that have nothing to do with the cpymn.org domain.
Hacking is a huge problem but you can deal with it if you catch it early on. Let’s move on to the prevention part.
How to Identify If Your Site was Hacked for Ranking Purposes
The first way to identify the problem is closely related to what I did in the example above. Simply set up a Google Alert for the words “site:domain.com”. This way you will be instantly notified by any new content indexed by Google, and if that content looks shady to you, you can take the necessary action to remove it as soon as possible, even before Google detects that it is actually a hack.
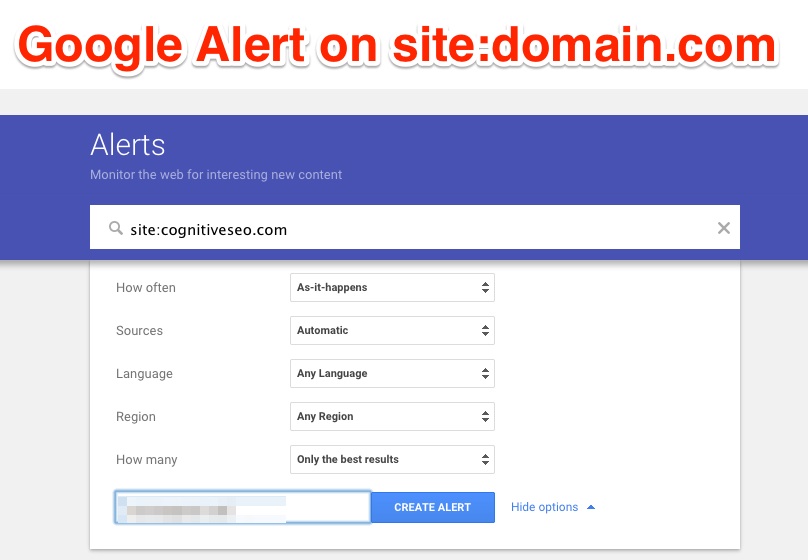
To set up an alert in Google you can access this page. In the query insert the “site:yourdomain.com” and I recommend to set it for As-it-happens to get instantly notified. You will receive the alerts on your email account and hopefully, you will have enough time to react to them should worst come to worst.
The second method to identify the hacking is with the help of Google Webmasters Tools. Inside the tool, you will be able to set up e-mail alerts in case Google detected that you’ve been hacked.
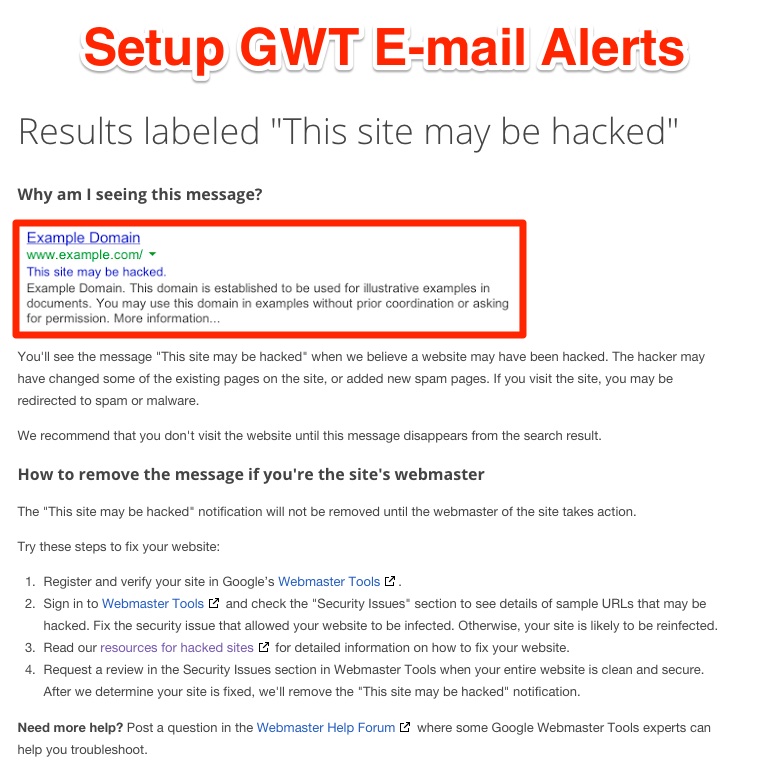
Unlike the first method in which you notice the hacking before Google, in this one it’s Google who discovers the hacking for you. It might be a bit later and action against your site could have already been taken, but it’s still a good way to discover it.
How to Secure Your Site
But as usual, the best way to protect yourself from hacking is making sure your website is unhackable (or really, really hard to hack). It’s worth to take the extra steps in order not to be an easy target for hackers.
1. Block WordPress Login
Start by limiting access to the “wp-admin” folder in WordPress. Allow only a selection of IP addresses to the login section of the WordPress login and redirect others to a page of your choosing.
This method will block automated scrapers to try brute force attempts at logging into your WordPress Login.
2. Use Only Trusted WordPress Plugins
I can’t stress enough this point, WordPress plugins have been a target for hackers since they were first introduced. In the summer of last year we witnessed a hacking of more than 50000 of websites, thanks to a WordPress plugin which had major security gaps in its code.
Unfortunately, there is no “trusted plugins only” tab in the plugin section for WordPress, but before installing any plugin to your website take some time to research it, its developers and see what other people think of it. This 30-minute research may save you a lot more hours in the future if you have to recover from a hacking.
3. Have a Backup Plan
There is great stress in having an online business and knowing that it could be hacked at any moment. A great treatment for this stress comes in the form of having daily backups for your website. You surely don’t want to wake up in the morning and by the time you take your first sip of coffee notice that your life’s work is off the grid. Such a waste of a good coffee.
Luckily there are many ways of backing it up. And the backups can be done automatically.
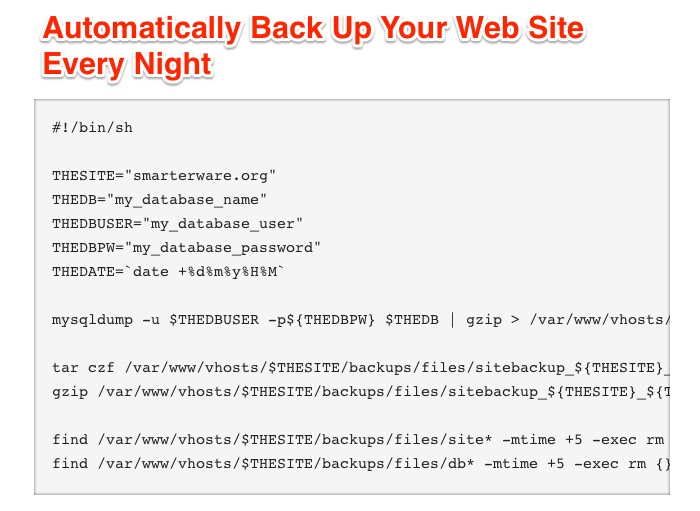
These few lines of code can give you the good night sleep you deserve. It only takes a couple of minutes to insert them into your server and you’ve covered the worse case scenario.
4. Use a Website Firewall
A great tool to add additional protection to your website is provided by the Sucuri team. This is one of the extra steps earlier. Not only that it gives extra protection against hacking attempts, it also provides defense against DDOS attacks. And as a plus, it offers Load Balancing and High Availability for your websites.
Setting up the Sucuri solution for WordPress is easy. All you have to do is install the plugin from the CMS Dashboard, activate it and configure it to your choosing. They even provide a quick guide for it here.
How does Google Tackle the Hacking Problem
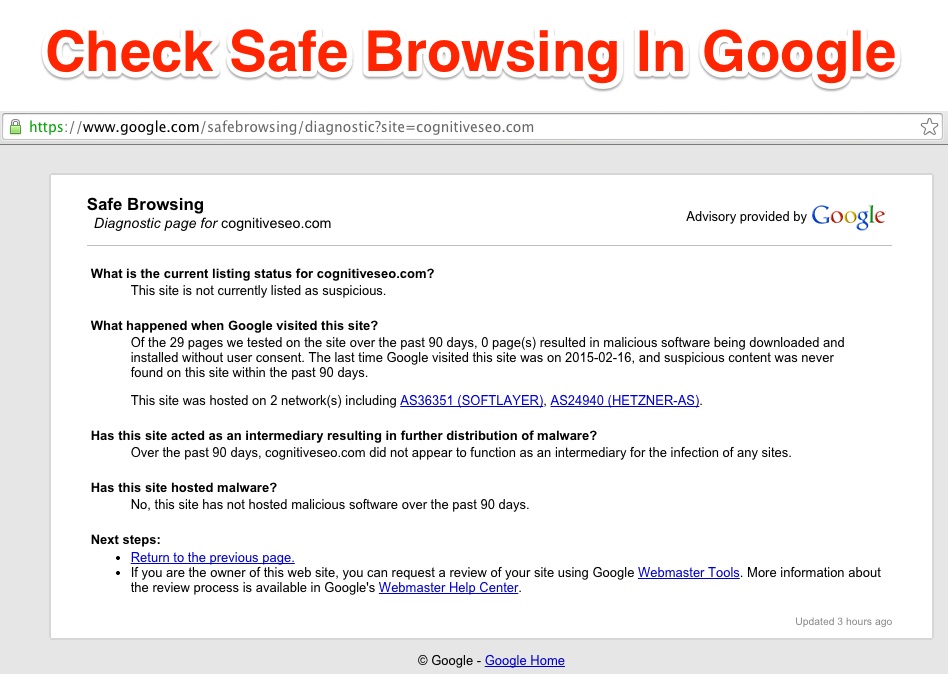
The Google service diagnoses your website for any malicious software. The Safe Browsing tool enables apps to verify URLs against Google’s constantly updated lists of suspected phishing and malware pages. Using this service, users will be notified before clicking on links that they will lead to malicious pages. It even prevents hackers to post the links to known phishing pages from your website.
How to Recover a Hacked Site
No matter how quickly a webmaster fixes the security issues, recovering from the penalties and hacking takes a while. Google is trying to make the recovery process easier for webmasters with the help of features like Security Issues, and a special section on the forums designated for hacked sites. They shared two interesting recovery stories in their latest blog post.
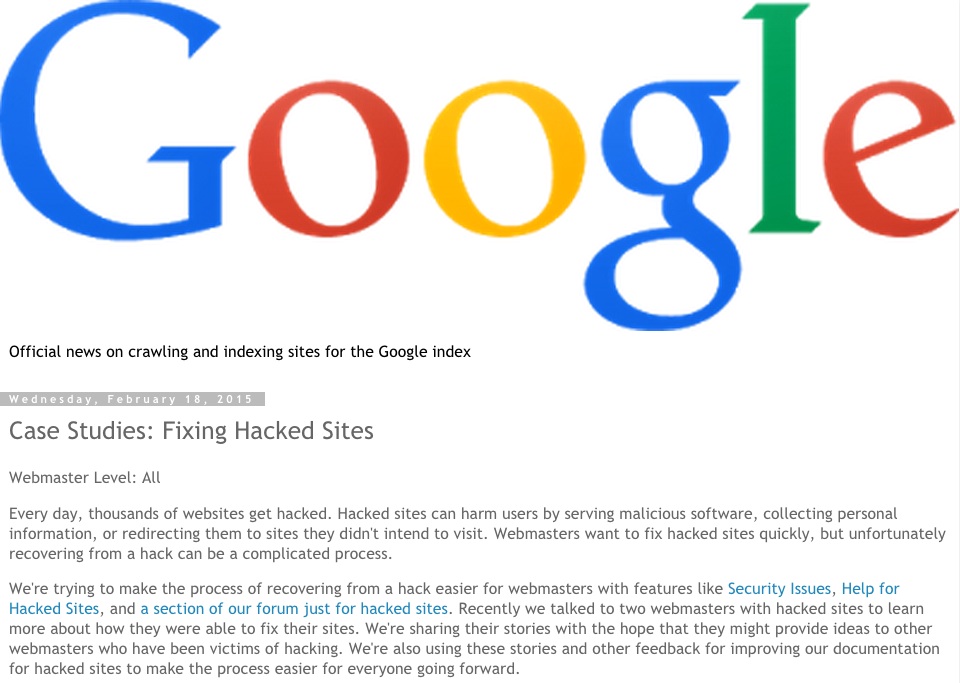
The first case was a WordPress user who received a notification in Google Webmasters Tools regarding their website being labeled as hacked. The webmaster found his code filled with “buy viagra” and “buy cialis” keywords”. Following the cleanup the webmaster had made, Google still warned him that there were still hacked scrips hidden inside the .htaccess file. Only after fixing that issue did Google remove the hacked site label.
The following are the steps the webmaster takes in order to keep his website clean:
- Keep the CMS updated to its latest version. The same goes for the plugins;
- Secure and strong password for the admin account;
- Two Step Verification for login (if it’s available);
- Install only verified and high reputation plugins.
The second case presented in the Google’s blog post is one in which a business owner had a hacker plant some pages on his domain. Hidden from GoogleBot the pages were untraceable using the “fetch as Googlebot” feature in WordPress. The webmaster finally fixed his issues and after a couple of reconsideration requests, Google removed the hacked label. Here are the following steps the webmaster takes in order to avoid being hacked:
- Use SFTP when transferring files;
- Secure access to the .htaccess file;
- Be vigilant and look for new and unfamiliar users in the admin panel or any place where users can modify the website.
Consequences of a Hacked Site
The aftermath of a hacked site is always hard to deal with. But it’s not impossible to recover from it. Let’s take this example from a forum member of WebmasterWorld.
In his case, just like many others, the hacking came from a pharma network and started inserting viagra/cialis pages on the user’s server. Hackers hid the pages from users, making them visible only for the search engine bots. They could have used a form of hacking like I have explained above in the article. The website was originally a WordPress site and the hackers managed to move it to Drupal and stopped inserting additional sites to the server after the migration.
The webmaster did not notice the hacking before Google did and it was hit by two Google penalties. One was received for the hacked pages, and one for unnatural links. Only after the Google penalties were sent the webmaster took action to remove the links from the webpage, disavow the unnatural hacked links using the disavow tool and send the first reconsideration request to begin the recovery process. As you can see from his report, Google did remove his unnatural link penalty. It was only after the second reconsideration request Google removed his hacked pages penalty.
We can draw some conclusions from the mishaps of this webmaster. Google understands that the unnatural backlinks pointing to your website are actually for the hacked pages. Even though it penalizes for both unnatural link profile and the hacked content, Google is willing to remove the penalties after you have taken action to correctly remove the problems on your website.
Conclusion
Going through a hacking problem is one of the most stressful and complex issues a webmaster will ever go through. Even if your business doesn’t rely too much on organic traffic, the penalties received from Google and having a note on your website that says “This site may contain malicious software” will ultimately bring heavy losses. I don’t want to sound too pessimistic about it, but hacking is a constant threat to online businesses. It’s best if webmasters spend a couple of hours to make sure the website is as secure as possible then spend weeks or even months to recover from hacking.
It’s encouraging to see that Google helps a lot in this matter, with the constant updates made to the algorithm, they will catch the hacks faster. Also, using the security tools available will make your website more secure and most of all you will have a backup plan to fall onto if worst comes to worst.
So what other ways or tools do you use for extra defense against hackers?
 Site Explorer
Site Explorer Keyword tool
Keyword tool Google Algorithm Changes
Google Algorithm Changes

I remember, couple of years back, one of my clients faced the same problem because of a wrongly intended web page uploaded to their server. I followed same steps by logging into Google webmaster tools. Though I wish web-hosts should strive to keep their machines clean and these hackers must have a hard time intruding into them.
it is also about the software you use. WordPress or other third party software that is out of the control of the actual hosts.
Great read. Sent these tips to some clients in addition to advice we’d already given regarding Google Alerts warnings and setting up Analytics tracking to monitor for problems.
I’m seeing it happen more and more which is disturbing.
glad to hear Adrian. some of the tips are easily implementable. like site:domain.
Hello Razvan.
My site is under Serp hijacking attack. Almost every two days there is a new hacked parasite site (that contains a scarped page of my site) in my serp place and it redirects to competitors site.
I email the parasite sites and their hosting and most of the times they remove the hack files after a few days but a new site keeps taking my serp. These parasite sites usually have a high PR and when Googlebot compares them with my site it caches them since they have higher PR.
I keep adding new content to my homepage everyday and fetch it and I add the hack backlinks to the Disavow list.
I have send Spam and Scraper reports to Google explaining the problem but there was no reaction.
This is going on for 4 months now and I don’t know what else to do.
Any ideas?
Thank you for your time.
so you site keep getting hacked every week? If this is the situation you should change your hosting providers maybe and asses the problems with your site. you should talk with someone specialized here.
Dear Razvan
My site is under SERP hijacking and its never been hacked.
The competitors hack other sites and they inject to them a file with a scraped homepage of my site so they confuse Googlebot and steal my SERP.
My site has never been hacked and its 100% clean.
The problem is that Google caches the hacked sites with the screped-copied pages instead on the original site.
understood. in that case you can not do anything until Google improves their algorithm 🙁 Just be sure to stay safe.
This is still a serious problem. My site has also been hit by SERP hijack. I wonder what are Google engineers doing even though this blackhat technique came to light back in 2009. This is disturbing.